We are still actively working on the spam issue.
Difference between revisions of "Tor"
(→Suggestions) |
(Google is a proper noun you clown) |
||
| (28 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
'''Tor''' is the name of several related and interconnected projects, all centered around providing you with [[Anonymising Yourself|anonymity]] and privacy online. In the simplest sense, '''Tor''' is the name of a free software project that protects your privacy online by bouncing your communications around a distributed network of computers (called "relays") run by volunteers all around the world. This network of relays is called the '''Tor Network'''. | '''Tor''' is the name of several related and interconnected projects, all centered around providing you with [[Anonymising Yourself|anonymity]] and privacy online. In the simplest sense, '''Tor''' is the name of a free software project that protects your privacy online by bouncing your communications around a distributed network of computers (called "relays") run by volunteers all around the world. This network of relays is called the '''Tor Network'''. | ||
| − | + | '''Tor Browser''' (previously '''Tor Browser Bundle''') is a web browser (forked from [[Firefox]]) that is pre-configured to protect your anonymity online. In the past it included related projects like Vidalia, TorButton and currently others that make browsing anonymously simple. Tor Browser is the only recommended browser to use with Tor. | |
Finally, '''The Tor Project''' is a 501(c)(3) non-profit (charity) organization that maintains and develops the Tor software and related projects. | Finally, '''The Tor Project''' is a 501(c)(3) non-profit (charity) organization that maintains and develops the Tor software and related projects. | ||
| Line 8: | Line 8: | ||
== Common misconceptions == | == Common misconceptions == | ||
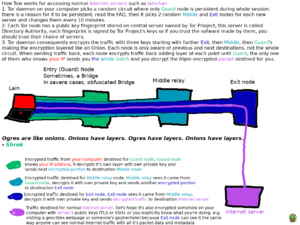
| + | [[File:How Tor Exit Nodes Work.png|thumb|left|How Tor Exit Nodes Work]] | ||
| + | Please watch the video [https://www.youtube-nocookie.com/embed/CJNxbpbHA-I ''The Tor Network''] by Jacob Applebaum and Roger Dingledine at the 30c3 (Chaos Communication Congress) in Hamburg, Germany. Applebaum and Dingledine are two of Tor's key people, and this talk will clear up any skepticisms and misconceptions you have. | ||
| − | Please | + | Please also take a look at Tor's [https://www.torproject.org/docs/faq.html.en Frequently asked questions]. |
| − | + | === Tor is illegal to use === | |
| + | |||
| + | {{Note|The USA attempted to secretly makes everyone who uses Tor and similar systems a suspicious individual. This would have meant that any person using Tor is not applicable to the Fourth or Fifth amendment of the US Constitution, as use of Tor is probable cause. You can read more about this [https://archive.is/mTcG3 here] and [https://archive.fo/ooPBe here]. The law has since been repealed.}} | ||
| − | + | It might be in places like the DPRK, or ISIS-controlled Syria. In places like Rwanda or the USA, it might make you a target of "law enforcement" by authorities that don't care about law and are more concerned with silencing enemies of The System. In places like Germany, Norway, Venezuela, Russia or any other reasonably sane country, you'll be perfectly fine. | |
| − | + | If you ''do'' live in a country that blocks Tor access, you can download Tor through the millions of mirror sites that exist. When using Tor, you can also use a bridge if they block (or monitor) Tor network connections. | |
| − | + | === The deep web is a dangerous place to browse, and you get "hackers" and viruses attacking you there === | |
The deep web or dark net are really just terms that are used in scaremongering. What they really refer to, is all the networking that can't be accessed via Google. Think about this for a second: this includes company and school intranets; hell, any network that you have to log in to to access is included here. Once you realise this, you realise that it's not as bad as once thought. It's also not as big. | The deep web or dark net are really just terms that are used in scaremongering. What they really refer to, is all the networking that can't be accessed via Google. Think about this for a second: this includes company and school intranets; hell, any network that you have to log in to to access is included here. Once you realise this, you realise that it's not as bad as once thought. It's also not as big. | ||
| − | + | Bottom-line, under the vague definition of "Darknet", anything not using ICANN (that is, the domestic Internet of the United States) is a "Darknet". | |
| + | |||
| + | === There's nothing but child porn and illegal stuff on Tor === | ||
| − | Firstly, people will continue to do this stuff regardless of whether or not Tor exists; people do it on the internet and in real life anyway, so this doesn't count. Secondly, Tor is also used by reporters, protesters, police officers, soldiers, and other people who just want to browse anonymously. | + | Firstly, people will continue to do this stuff regardless of whether or not Tor exists; people do it on the internet and in real life anyway, so this doesn't count. Secondly, Tor is also used by reporters, protesters, police officers, soldiers, and other people who just want to browse anonymously. Thirdly, there is that on clearnet just the same as on tor. Think of this: Everyday, drug smugglers use roads to transport their drugs. Does that make the roads themselves illegal? |
| − | + | While a few CP onion services exist on Tor (still not as much as on the clearnet), you won't come across these unless you look for them. International law makes it complex, but you probably will get arrested if you view such things '''with intent'''. If you view it by accident (such as clicking a random link that was posted to a hidden services thread), you have not committed a crime if you can prove that was the reason. Usually they won't find you anyway though (not to condone this activity). | |
| − | + | === It's too slow to stream/torrent over === | |
| − | + | Tor's speed comes from how many resources are provided by generous people. Also, [https://blog.torproject.org/blog/bittorrent-over-tor-isnt-good-idea Tor is not for torrenting over]. Torrenting over Tor not only leaks your IP address, but it also slows the network for literally everyone else. There is no point to torrenting over tor unless you're a dick trying to attack the network infrastructure. | |
| + | |||
| + | === I'll get arrested or get into trouble with my ISP or someone else for running Tor === | ||
You will only need to worry about this [https://www.torproject.org/docs/faq-abuse.html.en#TypicalAbuses if you are running a Tor exit node]. There are also some excellent resources created by the Tor staff; give them a read: | You will only need to worry about this [https://www.torproject.org/docs/faq-abuse.html.en#TypicalAbuses if you are running a Tor exit node]. There are also some excellent resources created by the Tor staff; give them a read: | ||
| Line 40: | Line 48: | ||
* [https://metrics.torproject.org/userstats-relay-country.html?graph=userstats-relay-country&country=us&events=off Direct Tor connections from the US] | * [https://metrics.torproject.org/userstats-relay-country.html?graph=userstats-relay-country&country=us&events=off Direct Tor connections from the US] | ||
* [https://metrics.torproject.org/userstats-relay-country.html?graph=userstats-relay-country&country=gb&events=off Direct Tor connections from the UK] | * [https://metrics.torproject.org/userstats-relay-country.html?graph=userstats-relay-country&country=gb&events=off Direct Tor connections from the UK] | ||
| − | * [https://metrics.torproject.org/userstats-relay-country.html?graph=userstats-relay-countrycountry=aq&events=off Direct Tor connections | + | * [https://metrics.torproject.org/userstats-relay-country.html?graph=userstats-relay-countrycountry=aq&events=off All Direct Tor connections] |
== Suggestions == | == Suggestions == | ||
| − | There are a few things to keep in mind while using | + | There are a few things to keep in mind while using Tor Browser: |
| − | + | === Correct usage === | |
| − | + | Make sure Tor Browser is configured correctly so that you're not leaking any information unknowingly. There are a number of websites you should use, such as [https://check.torproject.org/ this] simple webpage that checks if you're using Tor or not. If you view the webpage in Tor Browser, it should say: "Congratulations. This browser is configured to use Tor." [https://tor.stackexchange.com/questions/190/why-does-check-torproject-org-sometimes-tell-me-im-not-using-tor-when-i-am There are a few cases] when the website will give you a false positive, but for the most part, if everything is configured correctly, it should more often than not tell you that the Tor Browser Bundle is configured to use Tor. If not (for example, if you view the webpage in Firefox, Chrome, or other browsers not configured to use Tor), it should say: "Sorry. You are not using Tor." This website should be the first tool you check to make sure you're using the Tor Browser Bundle correctly. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | === Javascript === | |
| + | By default, [[JavaScript]] is enabled. There are a [https://www.torproject.org/docs/faq.html#TBBJavaScriptEnabled few reasons for this]; first and foremost, disabling JavaScript breaks a large number of websites in the clearnet, especially newer websites, as web developers have become reliant on using JavaScript for added usability and functionality. The other reason is, using NoScript to disable JavaScript globally but only whitelisting a few websites creates a unique fingerprint (everyone who uses NoScript this way whitelists different websites), which harms your anonymity. If usability is not a concern for you, '''we suggest simply disabling JavaScript altogether'''. Click the shield to the right of the domain bar, and select "safest mode" to disable JavaScript. | ||
| − | == | + | === Change default settings === |
| − | + | When using the background daemon, make sure to modify the torrc. The tor package in most repositories allow you to use it as a proxy. The package repositories (usually) don't have the browser. This package is just a daemon so you can proxy applications, such as [[Tox]] or [[IRC]]. On anything that you want proxied, set it to {{ic|localhost (or 127.0.0.1)}} for the address, {{ic|9050}} for the port, and the type of proxy it is, {{ic|SOCKS5}}. If you are proxying DNS, such as in Jitsi, it again is {{ic|localhost (or 127.0.0.1)}} for the address, but {{ic|64}} for the port. If you wish to use a different port for either of these, adjust your torrc file correspondingly. Please note that the {{ic|ControlPort}} is '''not''' a proxy port, but a port for other applications to control tor if you want it to, such as the package {{ic|tor-arm}}. | |
| − | + | == Controversy == | |
| + | ===Jacob Appelbaum=== | ||
| + | In 2016, a number of provably false claims of rape by Jacob Appelbaum were made. This was an obvious smear campaign. Nonetheless, almost immediately the Tor Project booted Jacob from the project permanently. The smear campaign was boosted by them. Jacob Applebaum has not been public for a long while since. | ||
== External links == | == External links == | ||
Latest revision as of 18:39, 9 May 2022
Tor is the name of several related and interconnected projects, all centered around providing you with anonymity and privacy online. In the simplest sense, Tor is the name of a free software project that protects your privacy online by bouncing your communications around a distributed network of computers (called "relays") run by volunteers all around the world. This network of relays is called the Tor Network.
Tor Browser (previously Tor Browser Bundle) is a web browser (forked from Firefox) that is pre-configured to protect your anonymity online. In the past it included related projects like Vidalia, TorButton and currently others that make browsing anonymously simple. Tor Browser is the only recommended browser to use with Tor.
Finally, The Tor Project is a 501(c)(3) non-profit (charity) organization that maintains and develops the Tor software and related projects.
Contents
- 1 Common misconceptions
- 1.1 Tor is illegal to use
- 1.2 The deep web is a dangerous place to browse, and you get "hackers" and viruses attacking you there
- 1.3 There's nothing but child porn and illegal stuff on Tor
- 1.4 It's too slow to stream/torrent over
- 1.5 I'll get arrested or get into trouble with my ISP or someone else for running Tor
- 2 Suggestions
- 3 Controversy
- 4 External links
Common misconceptions
Please watch the video The Tor Network by Jacob Applebaum and Roger Dingledine at the 30c3 (Chaos Communication Congress) in Hamburg, Germany. Applebaum and Dingledine are two of Tor's key people, and this talk will clear up any skepticisms and misconceptions you have.
Please also take a look at Tor's Frequently asked questions.
Tor is illegal to use
It might be in places like the DPRK, or ISIS-controlled Syria. In places like Rwanda or the USA, it might make you a target of "law enforcement" by authorities that don't care about law and are more concerned with silencing enemies of The System. In places like Germany, Norway, Venezuela, Russia or any other reasonably sane country, you'll be perfectly fine.
If you do live in a country that blocks Tor access, you can download Tor through the millions of mirror sites that exist. When using Tor, you can also use a bridge if they block (or monitor) Tor network connections.
The deep web is a dangerous place to browse, and you get "hackers" and viruses attacking you there
The deep web or dark net are really just terms that are used in scaremongering. What they really refer to, is all the networking that can't be accessed via Google. Think about this for a second: this includes company and school intranets; hell, any network that you have to log in to to access is included here. Once you realise this, you realise that it's not as bad as once thought. It's also not as big.
Bottom-line, under the vague definition of "Darknet", anything not using ICANN (that is, the domestic Internet of the United States) is a "Darknet".
There's nothing but child porn and illegal stuff on Tor
Firstly, people will continue to do this stuff regardless of whether or not Tor exists; people do it on the internet and in real life anyway, so this doesn't count. Secondly, Tor is also used by reporters, protesters, police officers, soldiers, and other people who just want to browse anonymously. Thirdly, there is that on clearnet just the same as on tor. Think of this: Everyday, drug smugglers use roads to transport their drugs. Does that make the roads themselves illegal?
While a few CP onion services exist on Tor (still not as much as on the clearnet), you won't come across these unless you look for them. International law makes it complex, but you probably will get arrested if you view such things with intent. If you view it by accident (such as clicking a random link that was posted to a hidden services thread), you have not committed a crime if you can prove that was the reason. Usually they won't find you anyway though (not to condone this activity).
It's too slow to stream/torrent over
Tor's speed comes from how many resources are provided by generous people. Also, Tor is not for torrenting over. Torrenting over Tor not only leaks your IP address, but it also slows the network for literally everyone else. There is no point to torrenting over tor unless you're a dick trying to attack the network infrastructure.
I'll get arrested or get into trouble with my ISP or someone else for running Tor
You will only need to worry about this if you are running a Tor exit node. There are also some excellent resources created by the Tor staff; give them a read:
- Running a Tor exit node for minimal harassment
- a list of template letters you can send to your ISP about Tor abuse
- A FAQ list on Tor abuse
You may also be interested in the Tor Metrics pages which will show you how common the use of Tor is in your country:
Suggestions
There are a few things to keep in mind while using Tor Browser:
Correct usage
Make sure Tor Browser is configured correctly so that you're not leaking any information unknowingly. There are a number of websites you should use, such as this simple webpage that checks if you're using Tor or not. If you view the webpage in Tor Browser, it should say: "Congratulations. This browser is configured to use Tor." There are a few cases when the website will give you a false positive, but for the most part, if everything is configured correctly, it should more often than not tell you that the Tor Browser Bundle is configured to use Tor. If not (for example, if you view the webpage in Firefox, Chrome, or other browsers not configured to use Tor), it should say: "Sorry. You are not using Tor." This website should be the first tool you check to make sure you're using the Tor Browser Bundle correctly.
Javascript
By default, JavaScript is enabled. There are a few reasons for this; first and foremost, disabling JavaScript breaks a large number of websites in the clearnet, especially newer websites, as web developers have become reliant on using JavaScript for added usability and functionality. The other reason is, using NoScript to disable JavaScript globally but only whitelisting a few websites creates a unique fingerprint (everyone who uses NoScript this way whitelists different websites), which harms your anonymity. If usability is not a concern for you, we suggest simply disabling JavaScript altogether. Click the shield to the right of the domain bar, and select "safest mode" to disable JavaScript.
Change default settings
When using the background daemon, make sure to modify the torrc. The tor package in most repositories allow you to use it as a proxy. The package repositories (usually) don't have the browser. This package is just a daemon so you can proxy applications, such as Tox or IRC. On anything that you want proxied, set it to localhost (or 127.0.0.1) for the address, 9050 for the port, and the type of proxy it is, SOCKS5. If you are proxying DNS, such as in Jitsi, it again is localhost (or 127.0.0.1) for the address, but 64 for the port. If you wish to use a different port for either of these, adjust your torrc file correspondingly. Please note that the ControlPort is not a proxy port, but a port for other applications to control tor if you want it to, such as the package tor-arm.
Controversy
Jacob Appelbaum
In 2016, a number of provably false claims of rape by Jacob Appelbaum were made. This was an obvious smear campaign. Nonetheless, almost immediately the Tor Project booted Jacob from the project permanently. The smear campaign was boosted by them. Jacob Applebaum has not been public for a long while since.