We are still actively working on the spam issue.
Difference between revisions of "Ghostleech"
m (minor text rearrangements) |
|||
| Line 4: | Line 4: | ||
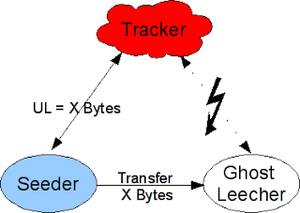
[[File:Ghostleeching.png|thumb|left|A sample ghostleeching scenario.]] | [[File:Ghostleeching.png|thumb|left|A sample ghostleeching scenario.]] | ||
| − | The bittorrent protocol is inherently insecure. This means that if I know the info_hash of a torrent and the IP+ Port that your torrent client is running on, I can connect to you and download the torrent from you, | + | The bittorrent protocol is inherently insecure. This means that if I know the info_hash of a torrent and the IP+Port that your torrent client is running on, I can connect to you and download the torrent from you, ''even if I am not a member of your private tracker''. |
In this scenario, the seeder is not you, but the peer you have scraped. By directly knowing the infohash and IP+Port, you are able to bypass the tracker and download from the seeder directly | In this scenario, the seeder is not you, but the peer you have scraped. By directly knowing the infohash and IP+Port, you are able to bypass the tracker and download from the seeder directly | ||
| Line 41: | Line 41: | ||
{{note| | {{note| | ||
| − | * It looks suspicious if you grab many .torrent files, but | + | * It looks suspicious if you grab many .torrent files, but don't actually download anything because you /ghostleeched/ it all. Many trackers automatically detect this. '''Mix up actual downloading with /ghostleeching/''' |
| − | *It is unsafe and suspicious to add a .torrent. Let it announce to a tracker (get peers) and then stop it. What you want to do is | + | *It is unsafe and suspicious to add a .torrent. Let it announce to a tracker (get peers) and then stop it. What you want to do is ''cultivate a list'' (IP+Port) of seedbox owners and "Archivers". The best way to do this is to download a torrent the normal way, but log all traffic. Sort by speed and you have your seedbox users |
| − | *With this list you can bypass steps 1-3. Add your torrent (IN A STOPPED STATE) | + | *With this list you can bypass steps 1-3. Add your torrent (IN A STOPPED STATE); remove the tracker; add your peers |
*It is risky to ghostleech on small swarms (<10 peers + Old torrents). Let the size of the swarm protect you}} | *It is risky to ghostleech on small swarms (<10 peers + Old torrents). Let the size of the swarm protect you}} | ||
| Line 51: | Line 51: | ||
==FAQ== | ==FAQ== | ||
| − | === | + | ===Scraping peers=== |
You want to build a list of seedboxes and Archivers. Don't do this manually. Download for a week normally, but log all your activity with iptraf or iftop. Then sort by speed to get your list | You want to build a list of seedboxes and Archivers. Don't do this manually. Download for a week normally, but log all your activity with iptraf or iftop. Then sort by speed to get your list | ||
| Line 60: | Line 60: | ||
*Use a utorrent DHT Patcher | *Use a utorrent DHT Patcher | ||
*Use an /old/ Azureus Peer Injector | *Use an /old/ Azureus Peer Injector | ||
| − | *Get the info_hash, convert to magnet link and add the magnet | + | *Get the info_hash, convert to magnet link and add the magnet URI |
| − | ===It takes | + | ===It takes a while for the torrent to start=== |
It can take up to 5 minutes. If the torrent hasn't started by then, your peers are bad. | It can take up to 5 minutes. If the torrent hasn't started by then, your peers are bad. | ||
| Line 72: | Line 72: | ||
===Notable cases=== | ===Notable cases=== | ||
| − | IPT was involved with a similar technique. They took peers from PTP/BTN, added them to their own tracker and | + | IPT was involved with a similar technique. They took peers from PTP/BTN/HDB, added them to their own tracker, and gave them to their own swarm (the IPT users) |
===Can I be banned for this=== | ===Can I be banned for this=== | ||
Revision as of 23:14, 31 December 2016
What is ghostleeching?
The bittorrent protocol is inherently insecure. This means that if I know the info_hash of a torrent and the IP+Port that your torrent client is running on, I can connect to you and download the torrent from you, even if I am not a member of your private tracker.
In this scenario, the seeder is not you, but the peer you have scraped. By directly knowing the infohash and IP+Port, you are able to bypass the tracker and download from the seeder directly
Case 1: You are NOT a member of a private tracker, but your friend is
If your IRC friend is on a /good/ private tracker and you are not. Just ask him for:
a) the torrent info_hash (eg: c12fe1c06bba254a9dc9f519b335aa7c1367a88a&dn)
b) an IP address:port of a seedbox user
Convert the infohash to a magnet link:
magnet:?xt=urn:btih:INFOHASH
magnet:?xt=urn:btih:c12fe1c06bba254a9dc9f519b335aa7c1367a88a&dn
and add that magnet link into your torrent client of choice and add the Peer using the given IP address:port
Congratulations! You are enjoying private tracker speeds, without private tracker autism.
Case 2: You ARE a member of a private tracker
Perhaps you want to download some files without taking a ratio hit:
- Grab a torrent.
- Pause the torrent or severely limit the download speed
- Write down all fast peers (IP and Port)
On a different IP:
- Add the torrent to your client
- Remove the tracker (which has your passkey and identifying information)
- Add the peers and you are good to go!
FAQ
Scraping peers
You want to build a list of seedboxes and Archivers. Don't do this manually. Download for a week normally, but log all your activity with iptraf or iftop. Then sort by speed to get your list
I can't add peers
Some clients prevent adding peers if you remove the private tracker. You have 4 solutions:
- Use a DHT-Patched client (utorrent serenity)
- Use a utorrent DHT Patcher
- Use an /old/ Azureus Peer Injector
- Get the info_hash, convert to magnet link and add the magnet URI
It takes a while for the torrent to start
It can take up to 5 minutes. If the torrent hasn't started by then, your peers are bad.
How can I detect if I was /ghostleeched/
No method at the moment. If you have a seedbox assume you were /ghostleeched/.
How can I prevent /ghostleeching/
Due to the protocol there is no easy way (other than stop using private trackers). You can try changing your ports every day. However this is not a reliable method, since the /ghostleecher/ will just grep your IP in the network logs to find the new port.
Notable cases
IPT was involved with a similar technique. They took peers from PTP/BTN/HDB, added them to their own tracker, and gave them to their own swarm (the IPT users)
Can I be banned for this
Yes. However, as a /ghostleecher/ in case 1 you have nothing to worry about since you can get a new IP. If you are providing the info_hashes+peers use your head.