We are still actively working on the spam issue.
Difference between revisions of "DNS"
m |
(turn into stub) |
||
| (24 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{ | + | {{Stub}} |
| − | + | '''Domain Name Systems''' convert domain names (e.g. wiki.installgentoo.com) into ip addresses (e.g. 176.9.127.115). By default, you're probably using your ISP's DNS. | |
| − | + | == Alternative DNS servers == | |
| + | If you're unhappy with your ISP's DNS services, consider the following: | ||
| − | + | ; OpenNIC | |
| + | : The [https://www.opennicproject.org/ OpenNIC Project] relies on volunteers to provide censorship free DNS servers. | ||
| + | : Click [https://www.opennicproject.org/nearest-servers/ here] to find the nearest OpenNIC servers. | ||
| − | + | ; Google DNS | |
| + | : 8.8.8.8 | ||
| + | : 8.8.4.4 | ||
| − | + | {{warning|[[Google]]'s DNS will, amongst other things, assign your IP to every site you visit and log it permanently! For more information click [https://developers.google.com/speed/public-dns/privacy here].}} | |
| − | |||
| − | + | == Problems with DNS == | |
| + | * DNS can be used for censorship. | ||
| + | [[File:dnsboobs.jpg|thumb|200px|right|Arab Spring protestor advising [[Google]]'s DNS to circumvent government censorship.]] | ||
| + | : The DNS owner can redirect any domain name to any IP address. This can happen due to siteblocking legislation (e.g. [[Wikipedia:Web_blocking_in_the_United_Kingdom |U.K.]]) or totalitarian governments (e.g. [[Wikipedia:Arab_Spring |Arab Spring]]). | ||
| + | : DNS is the simplest way to block a website from a tech illiterate user, and also the easiest site blocking method to circumvent. | ||
| − | + | * DNS can be used for Man in the Middle attacks. | |
| + | : If an attacker controls your DNS (e.g. poisoned WiFi), they can redirect your requests to malicious servers. HTTPS with valid certificates, DNSCrypt and servers that support the DNSSEC spec can protect against this, but tech illiterate users generally click through the security warnings. | ||
| − | + | == Securing DNS == | |
| + | *[[DNSCrypt]] | ||
| + | *[[Unbound]] | ||
| + | Main Article: [[Anonymizing_Yourself#DNS | Anonymising Yourself | DNS]] | ||
| − | + | == Running a DNS == | |
| − | + | While running a publicly available DNS is a bad idea (as with [[NTP]] servers, users will attempt to connect to you for years after you lose interest in hosting), you can easily run a DNS via [http://www.thekelleys.org.uk/dnsmasq/doc.html dnsmasq], [[Unbound]] and so on. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | == Redirect Everything to a Single Server == | |
| − | + | Redirecting all domain requests to a single server is easy with dnsmasq. Assuming your server is located at 192.168.1.1, your /etc/dnsmasq.conf file can be modified to: | |
| − | + | listen-address=192.168.1.1 | |
| − | + | address=/#/192.168.1.1 | |
| − | + | This is useful if you're running a [https://piratebox.cc/ PirateBox]esque server, where you only want users to see a single website. | |
| − | + | Any HTTPS website the user attempts to connect to will not work (that's HTTPS/CAs/Certs doing their job), but all HTTP servers will be redirected. | |
| − | + | [[Category:Terms]] | |
| − | + | [[Category:Networking]] | |
| − | + | [[Category:DNS]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Latest revision as of 18:11, 24 August 2019
Domain Name Systems convert domain names (e.g. wiki.installgentoo.com) into ip addresses (e.g. 176.9.127.115). By default, you're probably using your ISP's DNS.
Contents
Alternative DNS servers
If you're unhappy with your ISP's DNS services, consider the following:
- OpenNIC
- The OpenNIC Project relies on volunteers to provide censorship free DNS servers.
- Click here to find the nearest OpenNIC servers.
- Google DNS
- 8.8.8.8
- 8.8.4.4
Problems with DNS
- DNS can be used for censorship.
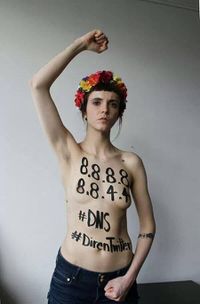
- The DNS owner can redirect any domain name to any IP address. This can happen due to siteblocking legislation (e.g. U.K.) or totalitarian governments (e.g. Arab Spring).
- DNS is the simplest way to block a website from a tech illiterate user, and also the easiest site blocking method to circumvent.
- DNS can be used for Man in the Middle attacks.
- If an attacker controls your DNS (e.g. poisoned WiFi), they can redirect your requests to malicious servers. HTTPS with valid certificates, DNSCrypt and servers that support the DNSSEC spec can protect against this, but tech illiterate users generally click through the security warnings.
Securing DNS
Main Article: Anonymising Yourself | DNS
Running a DNS
While running a publicly available DNS is a bad idea (as with NTP servers, users will attempt to connect to you for years after you lose interest in hosting), you can easily run a DNS via dnsmasq, Unbound and so on.
Redirect Everything to a Single Server
Redirecting all domain requests to a single server is easy with dnsmasq. Assuming your server is located at 192.168.1.1, your /etc/dnsmasq.conf file can be modified to:
listen-address=192.168.1.1 address=/#/192.168.1.1
This is useful if you're running a PirateBoxesque server, where you only want users to see a single website. Any HTTPS website the user attempts to connect to will not work (that's HTTPS/CAs/Certs doing their job), but all HTTP servers will be redirected.